Your Explain security architecture design in cloud computing images are available in this site. Explain security architecture design in cloud computing are a topic that is being searched for and liked by netizens today. You can Download the Explain security architecture design in cloud computing files here. Find and Download all royalty-free images.
If you’re looking for explain security architecture design in cloud computing images information connected with to the explain security architecture design in cloud computing topic, you have visit the right blog. Our site always gives you suggestions for refferencing the highest quality video and picture content, please kindly hunt and locate more informative video articles and images that fit your interests.
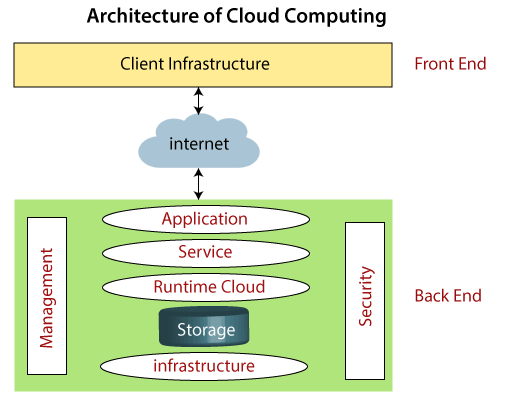
Explain Security Architecture Design In Cloud Computing. It is the back-end responsibility to provide data security for cloud users and the traffic control mechanism. Security and Privacy Security and Privacy of information is the biggest challenge to cloud computing. Cloud computing architecture is made of several layers for better operational efficiency. It consists of interfaces and applications that are required to access the cloud computing platforms.
 Cloud Computing Security Architecture Quantum Computing From quantumcomputingtech.blogspot.com
Cloud Computing Security Architecture Quantum Computing From quantumcomputingtech.blogspot.com
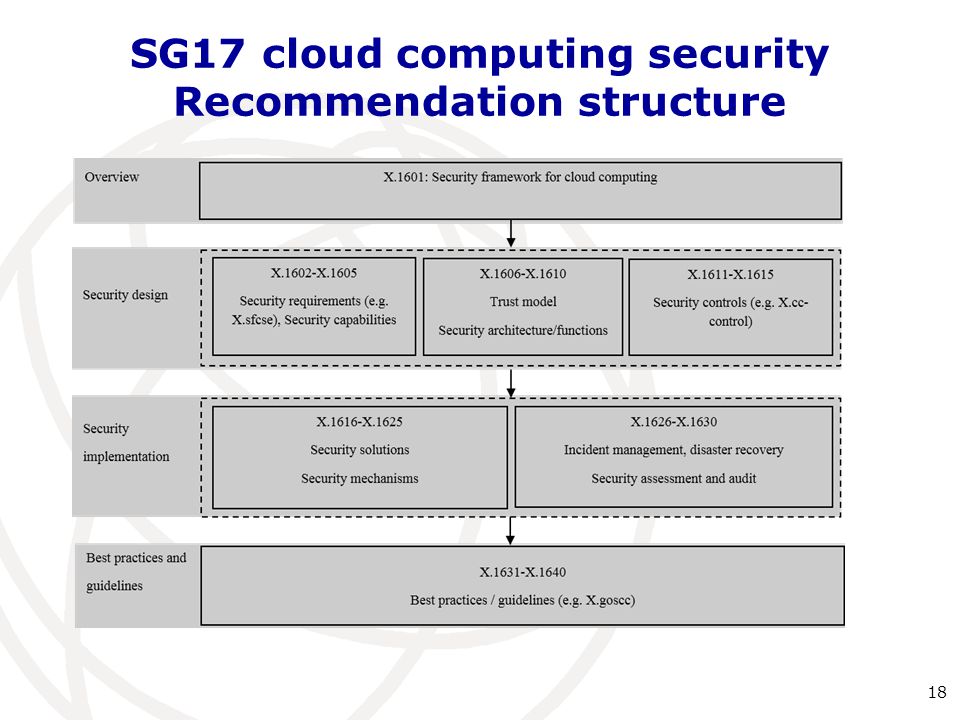
Security controls which can include technologies and processes. Cloud-enabled innovation is becoming a competitive requirement. The below diagram shows the architecture of cloud computing - Front End. The server also provides the middleware which helps to connect devices and communicate with each other. For the private cloud the key security principle that drives an effective design is that your design should seek to build a system of controls rather than a collection of controls. The Cloud Computing Architecture is the configuration of the system that involves local and cloud resources services middleware and software cloud clients and cloud storages networks geo-location.
The cloud architecture is composed of several components that combine together to form different layers of cloud architecture.
Start learning todays most in-demand skills for FREE. Figure - Cloud Computing Architecture. Cloud computing architecture is made of several layers for better operational efficiency. Cloud computing security architecture relies on having visibility throughout the cloud network with performance management capabilities. For the private cloud the key security principle that drives an effective design is that your design should seek to build a system of controls rather than a collection of controls. The front end is used by the client.

We can broadly divide the cloud architecture into two parts. The broad divisions of cloud architecture are. For the private cloud the key security principle that drives an effective design is that your design should seek to build a system of controls rather than a collection of controls. Security for ancient knowledge centers and cloud. The front end is used by the client.
 Source: researchgate.net
Source: researchgate.net
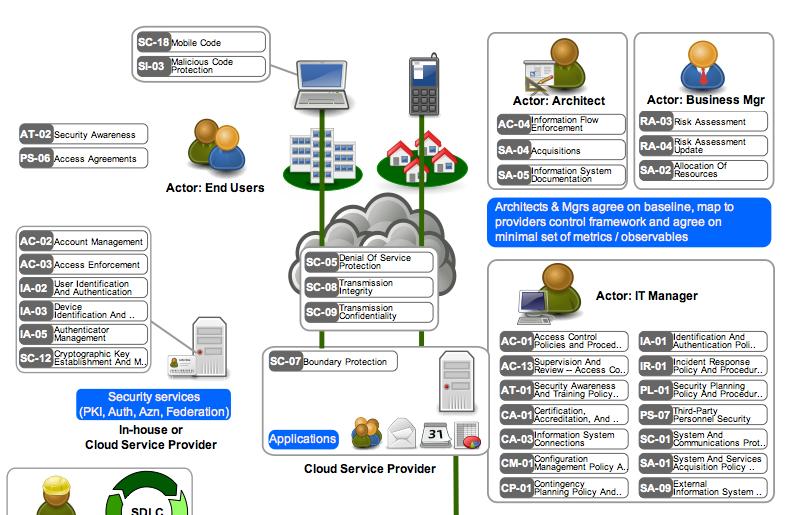
Security for ancient knowledge centers and cloud. This unified system of controls is more than just the individual security technologies and methodologies each part integrates with each other to provide the overall defenses. Trust boundaries between the different services and components deployed on the cloud. Cloud computing architecture is made of several layers for better operational efficiency. Security for ancient knowledge centers and cloud.
 Source: ibm.com
Source: ibm.com
Cloud Computing security architecture is categorized into frontend and backend along with an amalgamation of the event-driven architecture and the service-oriented architecture in Cloud Computing. The Cloud Computing Architecture is the configuration of the system that involves local and cloud resources services middleware and software cloud clients and cloud storages networks geo-location. Security for ancient knowledge centers and cloud. The cloud security architecture model is usually expressed in terms of. Trust boundaries between the different services and components deployed on the cloud.
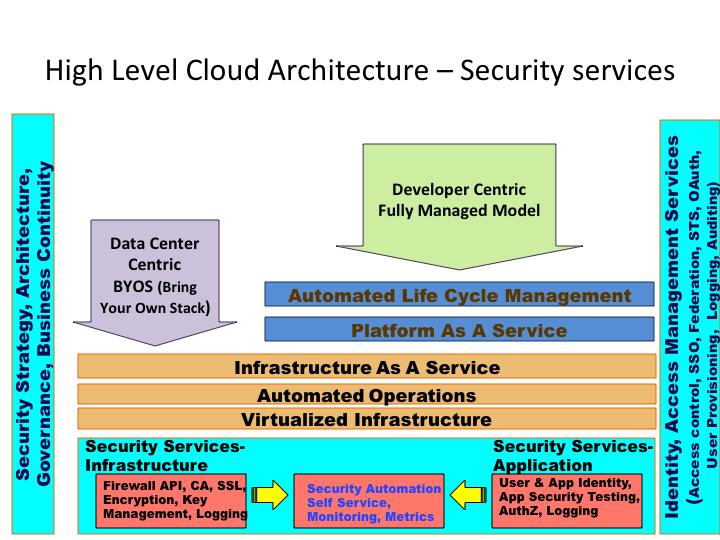
The cloud security architecture model is usually expressed in terms of. Cloud security architecture is a strategy designed to secure and view an enterprises data and collaboration applications in the cloud through the lens of shared responsibility with cloud providers. Cloud Architecture in Cloud Computing is a combination of several components and subcomponents that form together. Security and Privacy Security and Privacy of information is the biggest challenge to cloud computing. Cloud-enabled innovation is becoming a competitive requirement.
 Source: quantumcomputingtech.blogspot.com
Source: quantumcomputingtech.blogspot.com
In this paper we emphasize on various security threats in cloud computing also the existing methods to control them and explain the cloud computing along with its open secure architecture. The below diagram shows the architecture of cloud computing - Front End. These components typically consist of a front end platform fat client thin client mobileback end platforms servers storage a cloud based delivery and a network Internet Intranet Intercloud. The following diagram shows the graphical view of cloud computing architecture. The broad divisions of cloud architecture are.
 Source: security-and-privacy-reference-architecture.readthedocs.io
Source: security-and-privacy-reference-architecture.readthedocs.io
Security controls which can include technologies and processes. The Cloud Computing Architecture is the configuration of the system that involves local and cloud resources services middleware and software cloud clients and cloud storages networks geo-location. Cloud Computing security architecture is categorized into frontend and backend along with an amalgamation of the event-driven architecture and the service-oriented architecture in Cloud Computing. The broad divisions of cloud architecture are. Controls should take into account the location of each servicecompany cloud provider or third party.
 Source: ibm.com
Source: ibm.com
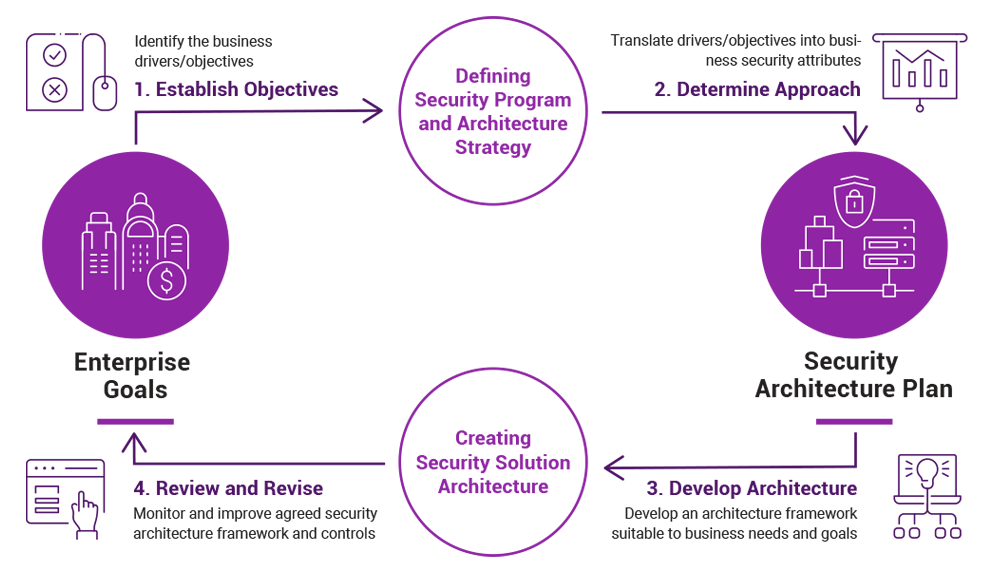
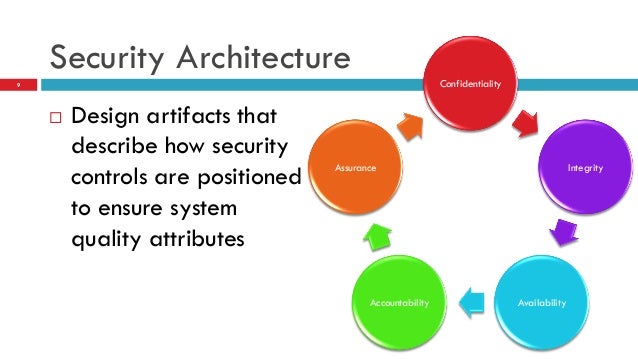
Security architecture is a unified security design that addresses the necessities and potential risks involved in a certain scenario or environment. It also specifies when and where to apply security controls. The cloud computing security is that the blend of the technologies and tips that the management is dependent upon basically portrays overseeing the consistency leads and secure infrastructure data applications safe-secure directions framework and information applications relates identifies to cloud computing use. Security and privacy issues can be overcome by employing encryption security hardware and. From Wikipedia the free encyclopedia Cloud computing architecture refers to the components and subcomponents required for cloud computing.
 Source: researchgate.net
Source: researchgate.net
This unified system of controls is more than just the individual security technologies and methodologies each part integrates with each other to provide the overall defenses. Cloud computing architecture is a combination of service-oriented architecture and event-driven architecture. Cloud controller or CLC is at the top and is used to manage virtualized resources like servers network and storage. The front end refers to the client part of cloud computing system. The Cloud Computing Architecture is the configuration of the system that involves local and cloud resources services middleware and software cloud clients and cloud storages networks geo-location.
 Source: quantumcomputingtech.blogspot.com
Source: quantumcomputingtech.blogspot.com
These components typically consist of a front end platform fat client thin client mobileback end platforms servers storage a cloud based delivery and a network Internet Intranet Intercloud. These components typically consist of a front end platform fat client thin client mobileback end platforms servers storage a cloud based delivery and a network Internet Intranet Intercloud. Security and privacy issues can be overcome by employing encryption security hardware and. Security and Privacy Security and Privacy of information is the biggest challenge to cloud computing. The broad divisions of cloud architecture are.
 Source: quantumcomputingtech.blogspot.com
Source: quantumcomputingtech.blogspot.com
In this paper we emphasize on various security threats in cloud computing also the existing methods to control them and explain the cloud computing along with its open secure architecture. Cloud computing architecture is made of several layers for better operational efficiency. Cloud-enabled innovation is becoming a competitive requirement. The Cloud Computing Architecture is the configuration of the system that involves local and cloud resources services middleware and software cloud clients and cloud storages networks geo-location. The design process is generally reproducible.
 Source: quantumcomputingtech.blogspot.com
Source: quantumcomputingtech.blogspot.com
Cluster Controller or CC manages the virtual networking between Virtual machines and external users. Cloud-enabled innovation is becoming a competitive requirement. It also specifies when and where to apply security controls. Walrus is the next layer and used as a storage controller to manage the demands of the users. Security controls which can include technologies and processes.
 Source: ibm.com
Source: ibm.com
The cloud security architecture model is usually expressed in terms of. The following diagram shows the graphical view of cloud computing architecture. The design process is generally reproducible. Cloud Computing security architecture is categorized into frontend and backend along with an amalgamation of the event-driven architecture and the service-oriented architecture in Cloud Computing. The front end is used by the client.
 Source: javatpoint.com
Source: javatpoint.com
The cloud security architecture model is usually expressed in terms of. Cloud computing architecture is divided into the following two parts - Front End. Start learning todays most in-demand skills for FREE. The front end is used by the client. Security and privacy issues can be overcome by employing encryption security hardware and.
 Source: security-and-privacy-reference-architecture.readthedocs.io
Source: security-and-privacy-reference-architecture.readthedocs.io
The front end is used by the client. Walrus is the next layer and used as a storage controller to manage the demands of the users. It consists of interfaces and applications that are required to access the cloud computing platforms. Security and privacy issues can be overcome by employing encryption security hardware and. It is the back-end responsibility to provide data security for cloud users and the traffic control mechanism.
 Source: quantumcomputingtech.blogspot.com
Source: quantumcomputingtech.blogspot.com
The cloud security architecture model is usually expressed in terms of. The below diagram shows the architecture of cloud computing - Front End. The cloud security architecture model is usually expressed in terms of. The cloud computing security is that the blend of the technologies and tips that the management is dependent upon basically portrays overseeing the consistency leads and secure infrastructure data applications safe-secure directions framework and information applications relates identifies to cloud computing use. The cloud architecture is composed of several components that combine together to form different layers of cloud architecture.
 Source: quantumcomputingtech.blogspot.com
Source: quantumcomputingtech.blogspot.com
It also specifies when and where to apply security controls. It contains client-side interfaces and applications that are required to access the cloud. Cloud computing architecture is a combination of service-oriented architecture and event-driven architecture. Figure - Cloud Computing Architecture. It also specifies when and where to apply security controls.

Security architecture is a unified security design that addresses the necessities and potential risks involved in a certain scenario or environment. The cloud security architecture model is usually expressed in terms of. The server also provides the middleware which helps to connect devices and communicate with each other. As more enterprises seek to accelerate their business by shifting data and. Controls should take into account the location of each servicecompany cloud provider or third party.
 Source: quantumcomputingtech.blogspot.com
Source: quantumcomputingtech.blogspot.com
Cloud computing architecture is divided into the following two parts - Front End. The cloud computing security is that the blend of the technologies and tips that the management is dependent upon basically portrays overseeing the consistency leads and secure infrastructure data applications safe-secure directions framework and information applications relates identifies to cloud computing use. Cluster Controller or CC manages the virtual networking between Virtual machines and external users. This unified system of controls is more than just the individual security technologies and methodologies each part integrates with each other to provide the overall defenses. It contains client-side interfaces and applications that are required to access the cloud.
This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site adventageous, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title explain security architecture design in cloud computing by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.






